What do Victoria Hoffman, Kay Weston, Angela Phinlay, and Rose Loomis have in common? They are all fictitious Hollywood characters played by Norma Mortenson. Not sure who Norma Mortenson is? She was better known as Marilyn Monroe.
Not all people who act out the role of another get to be famous, nor do they want to be. When it comes to life insurance, hiding one’s true identity when applying for coverage is a lucrative business so anonymity is important. Some of our actors steal the identity of another person and then play that person when applying for insurance. Other actors simply create a new, hybrid or synthetic identity when applying for insurance. The results are nearly the same – a minimal investment to purchase a life insurance policy wagering on the life of another with a large payout after just a few years. Thefts utilizing synthetic identities alone costs billions each year.
Nearly all systemic fraudulent attempts to purchase life insurance involves imposters wagering on the life of another who may or may not be a real person. Understanding how actors perpetrate their fraudulent and staged performances as insureds, along with utilizing the proper tools to detect such schemes, is key to stopping the attempted fraud before policies get issued. There are multiple techniques used to create these wagering contracts, and they typically involve either identity theft, the creation of a synthetic or hybrid Identity.
The Wagering Begins – Stealing an Identity
Perhaps the easiest way to wager on the life of another is to use the identity of an existing person who is ill or engaged in dangerous activities, and then apply for coverage as that person. Cases of identity theft are drastically increasing according to the National Council of Identity Theft Protection, and the insurance industry is not immune. Their estimates are that identity theft costs nearly $5.8 billion annually and rising. Typical identity validation techniques currently utilized to detect fraud at underwriting are designed to make sure the “insured’s” identity is a real one, and they validate that the proposed insured has a credit footprint. What it doesn’t tell the insurance company is that the insured is not the applicant.
To control communications from the insurance company, the perpetrator will provide false contact information for the insured. Instead, they will provide contact information that will lead any communication to the perpetrator. Also, some types of payment methods are preferred since the identity of the account holder is not readily available even if checked.
Some of the common victims of wagering contracts through stolen identities include unhealthy people known to the fraudster, closed community members, people in high-risk activities such as criminal activities or drug use, missing persons, or homeless persons.
For stolen identities on high-risk or unhealthy individuals, many tools on the market are useful in finding medical history such as prescription and lab checks, but these are not complete, and they will not contain information on tests that are scheduled to be performed (assuming that a potential target is seeking medical attention for something that appears suspicious). Unfortunately, systemic fraudsters also know how to circumvent these tools hence allowing the policies to pass health screening. The key is that they do not have to be successful all the time; rather, they just need to be successful some of the time.
Creating an Identity
Synthetic or hybrid identities may sound complicated, but in reality, are not. The creation of a synthetic identity involves creating a false digital footprint for someone who does not exist, or at least does not exist with the identifiers utilized. According to the ABA Banking Journal, the cost to the banking and financial institutions is $20 billion a year. [1] Once the identity is created, the perpetrator assumes that identity while applying for insurance coverage.
To create the synthetic identity that appears real and valid, the perpetrator must first create a digital footprint typically by applying for credit using the credentials desired for the new identity. Initially, the credit is denied, but even though the credit is denied, it creates a record with the credit bureaus. The more the applicant applies, the better the footprint, and ultimately, some form of credit gets approved. Payments are made on the debt thus furthering the creditworthiness of the synthetic person. Utilities bills may be moved into the name of the new identity thereby establishing additional payment and address history.
Synthetic identities are often difficult to detect since the identities are cultivated over a long period of time. Like stolen identities, the credit records portray a real identity. Once the digital ball gets rolling, it becomes much easier to further the footprint. Of course, there will be no medical records associated with the new identity. This allows the perpetrator to circumvent many of the medical validation tools used at underwriting to obtain insurance policies.
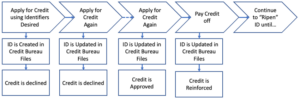
Once the policy is issued, the perpetrator will continue to pay the premiums, or they may sell the policy to others who are involved in similar schemes.
Collecting the Wagers
For the policies issued on persons whose identity was stolen, the hope is that the insured lives beyond the policy’s contestable period. For synthetic and hybrid identities, the perpetrator may have more control over when to report the death.
Once a death occurs, the perpetrator has several methods to assist in getting the claim paid. First, if the policy was issued insuring a real person using their stolen identity, then the perpetrator only needs to obtain the death certificate (assuming the insurer even requires one).
If the death occurs in the contestable period, the perpetrator will often claim to lack of legal authority to sign authorizations for the release of information thus frustrating the collection of records to confirm the information provided on the application. The beneficiary may also forbid contact with relatives who do have authority citing privacy concerns.
Other techniques to get claims paid is to switch the identity of a real person who is dying with the identity of the person on the application. Once the identity is switched, then the death certificate gets issued on the person who is insured and not the person who has died. Also, funeral homes rely on family members to provide the date of birth, social security number, and other identifiers for the death certificate, and they have no obligation to verify this information. This allows valid death certificates to get issued with the credentials matching the credentials of the insured per the application regardless of the validity of the information. In essence, the death certificate is a legitimate, certified certificate, but the data within the death certificate and death record is not accurate. Diligence has uncovered many cases where the date of birth is drastically different on the death certificate than in the medical and other records for the insured. If the claim is outside of the contestable period, then there is typically no predication to investigate, and many companies have express claim processes allowing the claims to speed through payment with little to no scrutiny.
Preventing the Fraud
Nearly all systemic life insurance fraud at time of underwriting involves an attempt at a wagering contract. To mitigate the risk of fraud due to wagering contracts, insurers must go beyond validating that the proposed insured has a real or valid digital identity. Once a wagering contract is issued, it can be difficult and expensive to defend against future claims that will inevitably happen earlier than expected. Insurers must take steps to validate that the applicant IS the insured at the time of underwriting.
Diligence has spent decades studying claims and identifying how fraudsters are able to obtain policies through deceit, and that expertise has been used to develop Prodigi, a software suite of tools that integrates into existing systems to screen applicants at the front before policies are issued.
Prodigi uses a proprietary set of algorithms and rules coupled with multiple data tools to identify wagering contracts. These tools include:
- Advanced location analysis including GPS coordinates of the exact address of the applicant
- Multiple subscription and propriety database interrogations to ensure consistency of the applicant’s data with the history of that applicant
- Fraud alert screening
- OFAC screening
- Voice “fingerprinting”
- Validating government-issued IDs and the consistency of the data between the ID and the applicant.
- Prodigi can even use selfies to compare against the government ID to insure they represent the same person.
The goal of Prodigi is to quickly and easily facilitate the issuance of policies with confidence while adding strong protective value against fraudulent applicants. The Prodigi record for the applicant can also be used for the life of the policy to prevent account takeovers. Stop the wagering contracts before they become a liability. For more information, contact Diligence International Group, LLC at (800) 660-4202 or Diligence@DIGroup-US.com, or visit the company’s website https://learning.digroup-us.com.
Diligence International Group, LLC, is a global leader in data verification and investigation services specializing in fraud detection, mitigation, and education for the insurance industry. Diligence offers an array of data verification solutions ranging from software solutions at time of underwriting, digital investigations and surveillance, to on-the-ground investigations in the United States and globally.
[1] ABA Banking Journal, Report: Synthetic Identity Fraud Results in $20 Billion in Losses in 2020, October 20, 2021, https://bankingjournal.aba.com…

